The Evolution of Cyber Threats: Notable Early Computer Viruses
Written on
Chapter 1: The Calm Before the Storm
In the early days of the internet, prior to the widespread use of smartphones, the online environment was relatively serene. However, it wasn't long before malicious actors, including governments and cybercriminals, began exploiting computer viruses for various agendas. This article will journey through some of the notable viruses from that era, examining malware, worms, and other intriguing attacks. The motivations for these viruses varied greatly, from promoting free internet access to attempting to dismantle a nation's nuclear capabilities. Join us on this captivating historical exploration.
The first video, "The 5 Worst Computer Viruses in History," highlights some of the most notorious malware incidents that have shaped the landscape of cybersecurity.
Section 1.1: Melissa Virus (1999, United States)
The Melissa virus was groundbreaking for its time, emerging when the internet was still largely uncharted territory in terms of cybersecurity risks. During an era dominated by floppy disks and early CD-ROM technology, this virus demonstrated a novel approach to propagation that caused significant disruption. Created by David L. Smith in Florida, the virus was disguised as a Word document containing passwords for adult content shared on a Usenet forum. When opened, it would email itself to 50 contacts from the user's address book, leading to a rapid and chaotic spread, especially as the world was bracing for Y2K.
Smith's use of a stolen AOL account ultimately led to his capture within a week, thanks to metadata in the document. He assisted the FBI in their investigations, resulting in a reduced sentence. The Melissa virus was estimated to have inflicted damages totaling around $70 million.
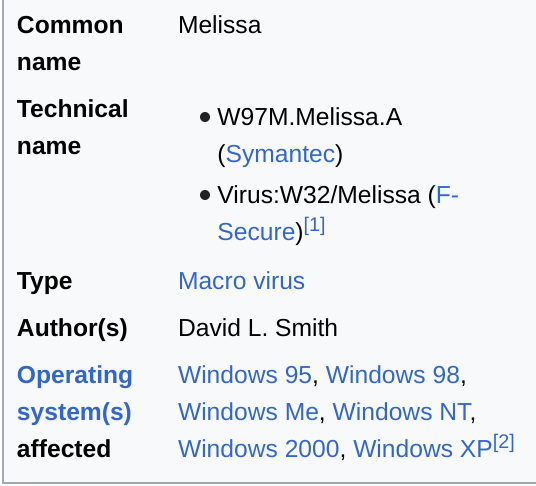
Wiki Extract for Melissa. Source: Wiki
Section 1.2: Anna Kournikova Virus (2001, Netherlands)
Just a few years after Melissa, the Anna Kournikova virus emerged, featuring an image of the famous tennis player. Developed in a matter of hours by a 20-year-old student named Jan De Wit, this Visual Basic worm made headlines not for corrupting data but for overwhelming email servers during its peak.
De Wit was caught after voluntarily surrendering, admitting he hadn't anticipated the virus's widespread impact. Initially charged with causing damage through data dissemination, he later received a job offer from the Dutch government. The Anna Kournikova worm is believed to have caused approximately $166,000 in damages.
The second video, "A Brief History of Computer Viruses," provides a concise overview of how computer viruses have evolved over the years.
Chapter 2: The Rise of Code Red and Other Threats
Section 2.1: Code Red (2001, Philippines)
Code Red emerged as a significant threat in the early 2000s, named after the Mountain Dew consumed by its creators. This worm exploited a buffer overflow vulnerability, allowing remote code execution across numerous machines. Remarkably, Code Red operated on a set schedule, executing specific actions at different intervals.
From July 1 to July 19, it sought to spread, followed by denial-of-service attacks on several IP addresses, including one associated with the White House. The infection peaked on July 19, affecting over 359,000 machines—an impressive figure for that time.
Section 2.2: Michelangelo Virus (1991, Australia)
The Michelangelo virus, an older threat, targeted DOS-based operating systems. Operating at the BIOS level, it did not interact with the operating system directly and had a unique time-based activation mechanism. On March 6, it would begin corrupting hard drive sectors by overwriting data with null values.
Despite its ominous name and association with the artist's birthday, there was no actual connection to Michelangelo in its code. The virus raised alarm bells in 1992 when several manufacturers shipped pre-infected systems, although the overall damage was relatively minimal.
Section 2.3: I LOVE YOU Worm (2000, Philippines)
Rounding out our list is the I LOVE YOU worm, also known as the Love Bug. Written in Visual Basic and released in early 2000, it aimed to steal passwords for free internet access. Its rapid spread was facilitated by the removal of geographic restrictions, leading to widespread damage.
At its height, it was estimated that 10% of global computer systems were infected, resulting in damages exceeding $5 billion. The chaos it caused forced numerous corporations to take their systems offline in a desperate attempt to contain the outbreak. Onel De Guzman, the author, faced legal consequences but was released due to outdated laws. In response, the Philippine government enacted the e-commerce law to address the growing issue of malware.
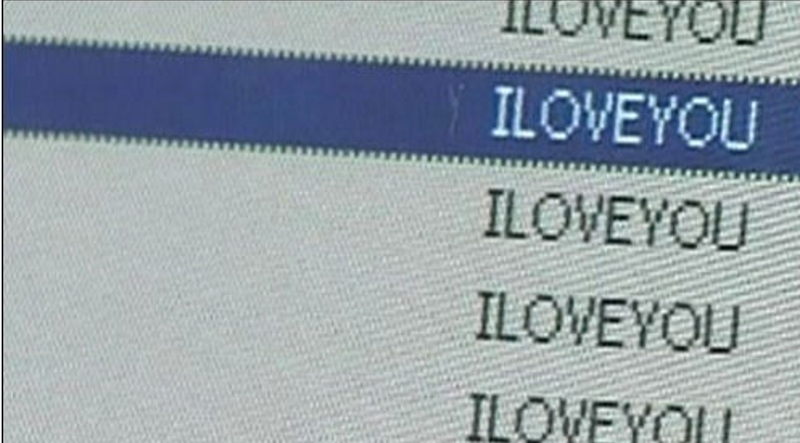
The Love Bug proliferated rapidly, leading to significant global disruptions. Source: Wiki
? Did you find this article informative? Join our community to support our work! ?
? Support us on Ko-fi: Investigator515
? Join our Telegram channel for exclusive updates or follow us on Twitter.
? Check out related articles: OSINT Unleashed: 5 Essential Tools for Cyber Investigators.